
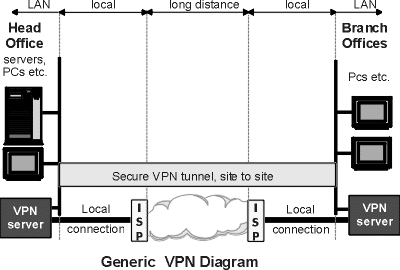
 Unlike
a private LAN, a VPN uses a public network infrastructure, usually the Internet,
to carry data between sites. These sites may be multiple different LANs, in
different buildings, in different cities, even in different countries. However,
to users on the network, the VPN makes all the sites behave as if they are
on one local private network.
Unlike
a private LAN, a VPN uses a public network infrastructure, usually the Internet,
to carry data between sites. These sites may be multiple different LANs, in
different buildings, in different cities, even in different countries. However,
to users on the network, the VPN makes all the sites behave as if they are
on one local private network.
A VPN creates a tunnel through the Internet by encapsulating and encrypting packets of data. Encapsulation involves wrapping packets inside a different kind of packet so the original packet is hidden. It also incorporates aspects of cryptography. The tunnel itself is first established through a process of authentication, where the identity of the source and destination is verified. All traffic travelling through the tunnel may be encrypted to ensure that it is private and secure.
ePipe supports three different types of VPNs that a site may wish to take advantage of as needs dictate. You can purchase these VPN feature keys separately. They include: -
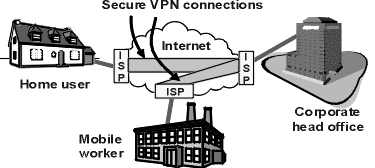 This
enables mobile or remote users to gain access to a central network through
the Internet. Most remote users are accessing the Internet, and in turn their
corporate network, from Windows PCs and notebooks. Point to Point Tunneling
Protocol (PPTP) is built into Microsoft's Dial-up Networking, which is included
with Windows 95, 98, NT and 2000. It is the easiest and most common method
of establishing a connection for casual VPN access.
This
enables mobile or remote users to gain access to a central network through
the Internet. Most remote users are accessing the Internet, and in turn their
corporate network, from Windows PCs and notebooks. Point to Point Tunneling
Protocol (PPTP) is built into Microsoft's Dial-up Networking, which is included
with Windows 95, 98, NT and 2000. It is the easiest and most common method
of establishing a connection for casual VPN access.
The PPTP suite and supporting functions are relatively lightweight; making them well suited to the processing resources of notebook computers and PCs. PPTP is known as a Layer 2 VPN and provides per-session authentication and optional encryption of data (MPPE).
ePipe acts as a PPTP Tunnel server (or terminator) and supports Microsoft Dial-up Networking PPTP clients accessing it through the Internet. The remote clients (or tunnel initiators) must be setup to use the public, fixed IP address of the ePipe at the central site.
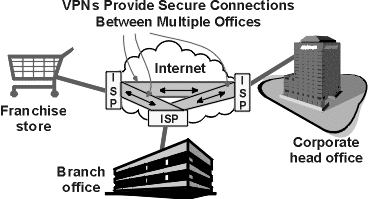 Site-to-site
VPNs typically require a Layer 3 VPN. The de facto standard for IP VPNs is
Internet Protocol Security (IPSec). A typical IP packet consists of headers,
which contain source and destination addresses, and the information payload.
Both of these contain confidential information. IPSec provides mechanisms
to protect both header and payload data for every packet transmitted across
the VPN. This verifies the identity of the sender and checks to see if the
packet has been modified en route. This makes it the best VPN solution for
site to site VPNs where the link is more likely to be active for extended
periods of time.
Site-to-site
VPNs typically require a Layer 3 VPN. The de facto standard for IP VPNs is
Internet Protocol Security (IPSec). A typical IP packet consists of headers,
which contain source and destination addresses, and the information payload.
Both of these contain confidential information. IPSec provides mechanisms
to protect both header and payload data for every packet transmitted across
the VPN. This verifies the identity of the sender and checks to see if the
packet has been modified en route. This makes it the best VPN solution for
site to site VPNs where the link is more likely to be active for extended
periods of time.
Any packets destined for another site must first pass through an IPSec security gateway. Every security gateway on the VPN must be interoperable with other security gateways and must therefore be IPSec-aware. In tunnel mode, IPSec provides site-to-site security between two security gateways, separated by a public network. However tunnel mode does not provide internal security between a workstation on the local LAN and the ePipe gateway. The IPSec Authentication Header (AH) and Encapsulating Security Payload (ESP) protocols can be used to protect either an entire IP payload or the upper-layer protocols of an IP payload. AH provides data integrity, source authentication and protection against replay attacks. ESP provides confidentiality, data integrity, and data source authentication and, protection against replay attacks. The authentication is provided through hash functions such as Message Digest 5 (MD5) and Secure Hash Algorithm (SHA).
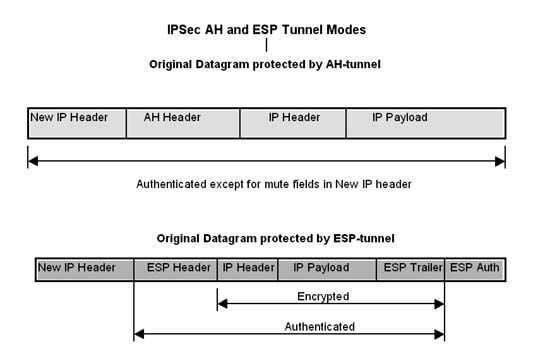
IPSec tunnel mode protects entire IP datagrams. In this case, the communications end points are specified in the inner header that's protected (i.e. the private LAN addresses) and the outer IP header specifies the tunnel end points (ePipe gateways), which provide de-capsulation and cryptographic functions. In AH-tunnel mode AH protects the outer IP header, original IP header and IP payload of the IPSec packet and does not provide confidentiality. On the other hand, in ESP-tunnel mode, ESP protects the original IP header and the IP payload but not the outer IP header. ESP also provides additional data confidentiality through negotiated encryption using a cipher with a symmetric shared key such as DES (56-bit), 3DES(168-bit) or Blowfish (128-bit). Therefore security gateways must possess enough processing power to manage the overhead imposed by strong authentication of each packet and bulk encryption of the information payload.
ePipe acts as an IPSec security gateway and secures private packets that traverse the multiple Internet connections within an end-to-end bonded (E2B) tunnel between remote sites. The ePipes are IPSec tunnel endpoints and make the logical connection between sites appear transparent to users on the local or remote LANs. Only one ePipe (i.e. central site) in a star-connected VPN needs to be a tunnel terminator and therefore it needs a public, fixed IP address. ePipe with SSV uses a number of private or shared keys to initiate sessions, sign packets and decrypt data. ePipe enforces the use of ESP so that data confidentiality is always available between sites. This suits the needs of most SMB VPNs that have a small number of remote branches and would find public key encryption infrastructure cumbersome.
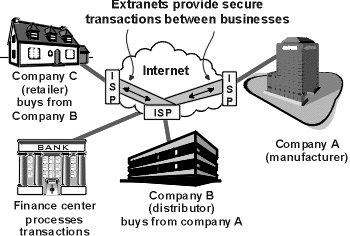 These
VPNs are often termed Extranets as they can allow third parties to access
parts of your network or conduct other forms of electronic transactions. To
properly establish a third party's identity, Internet Key Exchange (IKE) and
Public Key Encryption are often used. This involves the use of public and
private keys to sign packets and unlock encryption algorithms. IKE also supports
automatic key refresh, which further improves security.
These
VPNs are often termed Extranets as they can allow third parties to access
parts of your network or conduct other forms of electronic transactions. To
properly establish a third party's identity, Internet Key Exchange (IKE) and
Public Key Encryption are often used. This involves the use of public and
private keys to sign packets and unlock encryption algorithms. IKE also supports
automatic key refresh, which further improves security.
A system that supports this is often called Public Key Infrastructure (PKI) and involves electronic credentials (also called Digital Certificates - or public keys) and a trusted third-party Certificate Authority (CA) that verifies and authenticates the validity of every party involved in an electronic transaction. PKI can provide the security required when conducting electronic business across the Internet. PKI is also useful for large VPNs in order to manage authentication in a scalable manner. Certain organizations may choose not to use a third party certificate authority but have their own in-house server computer that acts as a certificate authority. This would play the key role in the authentication of all their branches wishing to connect to HQ through their VPN.
ePipe will soon support PKI with digital certificates (PKIX) once aspects of X.509 certificate management are refined. If each party uses an ePipe as the IPSec security gateway then they can also use E2B to increase bandwidth by bonding multiple Internet connections together. If one end however is not an ePipe, then they can only use the bandwidth available through one physical connection to the ISP at each location.
![]()
about ePipe | products | solutions | support | information center | contact us
Copyright © 2002 ePipe Pty. Ltd. All rights reserved.