
Transmission Control Protocol/Internet Protocol (TCP/IP) is an industry-standard suite of protocols designed to connect networks of different sizes whether they be next door or around the globe. TCP/IP is a suite of protocols that have been developed over many years and are now widely used in most operating systems and many software products. The largest example of a network that uses the TCP/IP protocol is, of course, the Internet.
Networks are divided into two general groups called Local Area Networks (LAN) and Wide Area Networks (WAN).
LANs are networks within a building and typically are high speed networks that connect computers, printers and other network devices together. Ethernet is the most commonly implemented LAN and typically has a speed of either 10Mbps or 100Mbps. These days, Ethernet networks are typically constructed of Category 5 UTP cables and hubs (concentrators) and switches. The devices connected to the Ethernet network are attached to one end of the UTP cable and the other is attached to the hub or switch. It is the task of the hub or switch to transmit the packets of information sent by all devices to some or all of the other devices connected to the Ethernet LAN.
WANs are networks that span the distance between buildings, cities and even countries. WANs are LANs connected together using wide area network services from telecommunications carriers and typically use technologies such as standard phone lines (called POTS (Plain Old Telephone Service) or PSTN (Public Switched Telephone Network)), ISDN (Integrated Services Digital Network), Frame Relay, ATM (Asynchronous Transfer Mode) or other high speed services.
The picture below shows a typical WAN consisting of 2 LANs connected together using services provided by a telecommunications carrier.
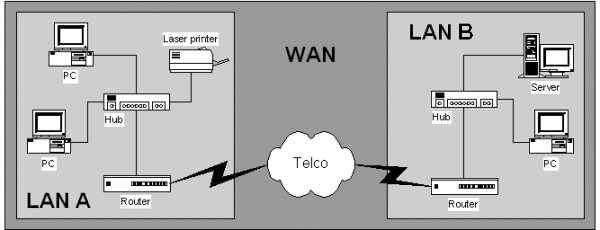
WANs are typically connected using routers which connect the LAN to the telco at each site. It is the job of the router to forward data from the LAN to the WAN and vice versa.
TCP/IP is based on a four-layer reference model. All protocols that belong to the TCP/IP protocol suite are located in the top three layers of this model. Each layer is in charge of a set of network functions designed to move data across a network.
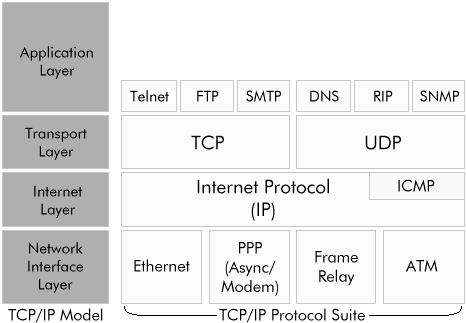
The 4 layers are described in the table below.
| Layer | Description | Protocols |
| Network Interface | This layer specifies how data is physically transmitted across the network and includes specifications for the hardware that connects the device to the cable, the cable media itself and all the connecting hardware. | Ethernet, Serial, Frame Relay, ATM, etc. |
| Internet Layer | Sometimes called the network layer as the protocols in this layer are responsible for the sending and receiving the data on the network and for deciding how packets of data get from one network to another (called routing). | IP, ICMP, ARP |
| Transport Layer | This layer is responsible for ensuring reliable delivery of data from end to end and for other connection management activities. | TCP, UDP |
| Application Layer | This layer defines how TCP/IP applications talk to or use the transport layer in order to effectively communicate across the network. | HTTP, Telnet, FTP, SNMP, DNS, SMTP, HTTP and many others |
In this TCP/IP primer we will discuss the different protocols that make up the TCP/IP suite and how they work as well as give you enough information to enable you to design your own IP network.
Any device or computer on a network may want to talk to any other device on that or any other connected network. To achieve this every device connected to the network must have a unique address, just like using a postal service. No two computers may have the same address as the device sending the data will not know which device to send it to.
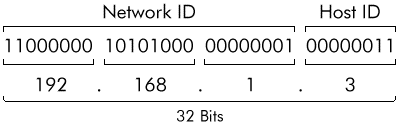
The TCP/IP suite of protocols uses the IP protocol to handle all addressing and routing issues. An IP address is a unique number that identifies each host (computer or TCP/IP device) to the network. The IP address is made up of 2 parts called the network ID and the host ID. The network ID identifies the network on which the host is located. The host ID is the identifier for the host on that network.
The IP address is a 32 bit number. An example of an IP address in binary would be:
11000000 10101000 00000001 00000011
To make IP addresses easier to read they are represented as four 8 bit numbers that are converted to decimal format and separated using periods ("."). This format is referred to as dotted decimal notation. Thus the address above would be shown as:
192.168.1.3
Note: Click here for more information on converting IP addresses to or from binary format.
This address is made up of the nework and host IDs. The diagram below illustrates this example IP address in both binary and dotted decimal notation and shows the network and host ID parts of the address. Each group of 8 bits is referred to as an octet. Thus an IP address is made up of 4 octets.
There are two special case addresses that cannot be used for any device on a network. These addresses are called the network address and the broadcast address. The network address for any given network is the network ID and all zeros in the host ID. Thus for our example above, the network address would be
192.168.1.0
or
11000000 10101000 00000001 00000000
The broadcast address is a special address used when one node wants to send something to all other nodes on the same local network. The broadcast address consists of the network ID and all ones in the host ID. Thus for our example, the broadcast address would be:
192.168.1.255
or
11000000 10101000 00000001 11111111
Neither of these addresses should ever be used for nodes on the network.
The Internet community has defined five address classes. Class A, B, and C addresses are used for assignment to TCP/IP nodes. Classes D and E are not typically used for nodes on the network. The class of address defines which bits are used for the network and host ID parts of each address. The address class also defines how many networks and hosts per network can be supported. If we define a.b.c.d as an IP address then the table below shows the range of addresses, network and host portions of the IP address, number of networks and number of hosts per network for each class of IP address.
| Class | Address Range of first octet |
Network ID | Host ID | Number of Networks |
Number of hosts per network |
| A | 1 to 126 | a | b.c.d | 126 | 16777214 |
| B | 128 to 191 | a.b | c.d | 16384 | 65534 |
| C | 192 to 223 | a.b.c | d | 2097152 | 254 |
| D | 224 to 239 | n/a | n/a | n/a | n/a |
| E | 240 to 254 | n/a | n/a | n/a | n/a |
Thus IP address 192.168.1.3 is a class C address, its network ID is 192.168.1 and its host ID is 3.
The network and broadcast addresses for each network class are listed in the table below:
| Class | Network Address | Broadcast Address |
| A | X.0.0.0 | X.255.255.255 |
| B | X.X.0.0 | X.X.255.255 |
| C | X.X.X.0 | X.X.X.255 |
where X is a valid number for that address class.
Network IDs and host IDs are identified using a subnet mask which is a series of 1s and 0s that match the network and host portion of the address respectively. Thus for a C class IP address, the subnet mask would be:
11111111 11111111 11111111 00000000
In dotted decimal notation this would be:
255.255.255.0
So, for class A, B and C addresses, the corresponding subnet masks would be:
| Class | Subnet Mask in Binary | Subnet Mask in Decimal |
| A | 11111111 00000000 00000000 00000000 | 255.0.0.0 |
| B | 11111111 11111111 00000000 00000000 | 255.255.0.0 |
| C | 11111111 11111111 11111111 00000000 | 255.255.255.0 |
These subnet masks are the default masks for their respective class. Customising the subnet mask for a given network is called subnetting. You subnet a network when you need to create more than one network from a single network. To connect networks together you need a device called a router which moves IP packets from one IP network to another.
When assigning addresses to your nodes you must ensure that all nodes on the same IP network get a unique IP address that has the same network ID as every other node on that network.
Note: Click here for more information on converting IP addresses to or from binary format.
Classless Inter-Domain Routing (CIDR)
CIDR is a new addressing scheme for the Internet which allows for more efficient allocation of IP addresses than the old Class A, B, and C address scheme.
As Internet addresses were generally only assigned in the three previously mentioned classes (A, B or C), there were many wasted addresses. For example, if you needed 100 addresses you would be assigned the smallest address class (C), but that still meant 154 unused addresses. The overall result was that while the Internet was running out of unassigned addresses, only 3% of the assigned addresses were actually being used. CIDR was developed to be a much more efficient method of assigning addresses.
Restructuring IP Address Assignments
Classless Inter-Domain Routing (CIDR) is a replacement for the process of assigning Class A, B and C addresses with a generalized network identifier or prefix. Instead of being limited to network prefixes of 8, 16 or 24 bits, CIDR currently uses prefixes anywhere from 13 to 27 bits. Thus, blocks of addresses can be assigned to networks as small as 32 hosts or to those with over 500,000 hosts. This allows for address assignments that much more closely fit an organization's specific needs.
The table below shows the number of Class C networks and hosts equivalent to CIDR block prefixes:
| CIDR Block Prefix |
Number of Equivalent Class C Networks |
Number of Host Addresses |
| /27 |
1/8th of a Class C |
32 hosts |
| /26 |
1/4th of a Class C |
64 hosts |
| /25 |
1/2 of a Class C |
128 hosts |
| /24 |
1 Class C |
256 hosts |
| /23 |
2 Class C |
512 hosts |
| /22 |
4 Class C |
1,024 hosts |
| /21 |
8 Class C |
2,048 hosts |
| /20 |
16 Class C |
4,096 hosts |
| /19 |
32 Class C |
8,192 hosts |
| /18 |
64 Class C |
16,384 hosts |
| /17 |
128 Class C |
32,768 hosts |
| /16 |
256 Class C = 1 Class B |
65,536 hosts |
| /15 |
512 Class C |
131,072 hosts |
| /14 |
1,024 Class C |
262,144 hosts |
| /13 |
2,048 Class C |
524,288 hosts |
IP Addresses in CIDR Form
A CIDR address includes the standard 32-bit IP address and how many bits are used for the network prefix (i.e. the number of bits that define the network part of the IP address, usually defined by the subnet mask). For example, in the CIDR address 206.13.1.48/25, the "/25" indicates the first 25 bits are used to identify the unique network IP address, leaving the remaining bits to identify the specific host within that network.
CIDR employs a simpler way of writing IP addresses and their corresponding subnet masks than writing the IP address and subnet mask separately. For example, a host with an IP address of 192.168.5.8 and a subnet mask of 255.255.255.0 would be written in CIDR form as 192.168.5.8/24. The table below shows how the subnet mask corresponds to the number of subnet bits used in the CIDR form of the IP address.
| Subnet Mask (decimal) |
255 |
255 |
255 |
0 |
| Subnet Mask (Binary) |
11111111 |
11111111 |
11111111 |
00000000 |
| Number of subnet bits |
8 |
8 |
8 |
0 |
| Total number of subnet bits |
24 (8 + 8 + 8) |
|||
When creating a new network you have several choices to make before assigning addresses to your computers and other IP nodes. Firstly you should decide whether you need to use private IP addresses or real or Internet Assigned IP addresses.
Particular addresses in each address class have been reserved for private IP networks. These address ranges are listed in the table below:
| Class | Reserved Address | Addresses in this range |
| A | 10.X.X.X | 10.0.0.1 to 10.255.255.254 |
| B | 172.16.X.X to 172.32.X.X | 172.16.0.1 to 172.32.255.254 |
| C | 192.168.X.X | 192.168.0.1 to 192.168.255.254 |
These address ranges are designed for internal use and will not be routed through the Internet. When designing a small to medium size network it is common to use the 192.168 series of addresses.
If you need routable or real Internet assigned IP addresses you should contact your ISP for a series of addresses. When connecting your network to the Internet, typically you will only need a few real addresses for the devices that actually connect your network to the Internet and for web and email servers or firewalls. The rest of your network is usually hidden behind a router or firewall that does Network Address Translation (NAT). See NAT for more information.
When selecting your network address you need to know two things:
Answering these questions will help you decide what class of address you should use and how you should subnet that address. Subnetting will be explained further later.
When determining the number of separate IP sub-networks in your overall LAN or WAN you need to count each separate physical network that is separated by a router. This includes networks between routers that maybe point-to-point links. Thus the network between two routers, across a wide area service such as ISDN or Frame Relay, is a separate IP network and needs to be counted.
If you have no more than 254 nodes in any single IP network then you can use C class addresses for each. If you have more than 254 nodes per network then you will need to use an A or B class IP network and, probably, use subnetting to achieve an efficient design. Using supernetting is another option but beyond the scope of this primer.
When designing an IP network so that addresses can be allocated to nodes, it is frequently necessary to take your existing address alocation and split it up into multiple networks. The process of creating smaller networks from a single larger IP network is called subnetting and the resultant IP networks are called subnets. There are various reasons for needing to subnet an existing network. These include:
Once again, to subnet a network you need to know:
Lets use an example to illustrate the subnetting process. Assume you have been assigned a B class network address of 150.3.0.0 which has a default subnet mask of 255.255.0.0. This network, without subnetting would support a maximum of (256 x 256) - 2 = 65534 nodes (we subtract the 2 because the network and broadcast addresses are not valid addresses for nodes). By any standard, a network with over 60,000 nodes is a large network and it would be very unlikely that a single IP network could handle this number of nodes due to performance and managability issues.
Lets say that your network has no more than 200 nodes per separate network. A simple way of subnetting this network would be two simply increase the subnet mask to include the 3rd octet of the address. That is, the subnet mask for your network would be 255.255.255.0. This would create 254 networks within the 150.3.0.0 network. These networks would be numbered as follows:
150.3.1.0
150.3.2.0
150.3.3.0
....
150.3.254.0
The diagram below shows how the host ID has been reduced to the last octet and the 3rd octet is now used for the subnet ID. In this example we have an address of 150.3.32.18 which would be node 18 on subnet 32 in network 150.3. This subnet is more correctly referred to as 150.3.32.0 with subnet mask 255.255.255.0.
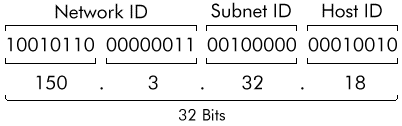
Each of these subnets can have up to 254 nodes.
In more general terms, a network can be subnetted using any pattern of 0s and 1s in the host portion of the subnet mask. Lets look at another example. If we had a C class network using address 192.168.5.0 which has a default subnet mask of 255.255.255.0. We could subnet this network into smaller networks. Lets say we need 4 separate networks. To subnet this network into 4 networks we need to look at the subnet mask in binary or bit form:
11111111 11111111 11111111 00000000
The last octet (the host ID portion of the IP address for a C class network) can be split into a subnet ID and host ID. To provide 4 subnets we can use the table below to find out the subnet mask we need to use. This table shows the various subnet masks for a C class address that can be used. Once again note that the all zeros and all ones addresses are not allowed thus 2 addresses have been deducted from each network.
| Subnet Mask | Number of Networks |
Number of Nodes per Network |
||
| 1st - 3rd Octets | 4th Octet | |||
| Binary | Decimal | |||
| 255.255.255 | 00000000 | 0 | 1 | 254 |
| 255.255.255 | 11000000 | 192 | 2 | 62 |
| 255.255.255 | 11100000 | 224 | 6 | 30 |
| 255.255.255 | 11110000 | 240 | 14 | 14 |
| 255.255.255 | 11111000 | 248 | 30 | 6 |
| 255.255.255 | 11111100 | 252 | 62 | 2 |
So to obtain a network with 4 subnets we would need to use a subnet mask of 255.255.255.224 which gives you a maximum of 6 networks, each supporting up to 30 nodes. If 30 nodes is too few to support a network then you will need to consider using more than one C class network or using a B class network.
Let us look at some examples of how to allocate IP addresses to a network.
Lets take the simplest case where company XYZ needs to connect to the Internet to allow their staff to browse the web and use e-mail. The company has 20 computers on a single existing LAN and the company has no other sites.
In this situation you only need one IP network to allow all the computers on this single LAN to talk to each other. As you saw earlier, a single private C class address will support up to 254 addresses. So, selecting a network address of 192.168.1.0 would fill the needs of company XYZ. Each computer (including the router) could then be allocated addresses like:
192.168.1.1
192.168.1.2
192,168.1.3 etc...
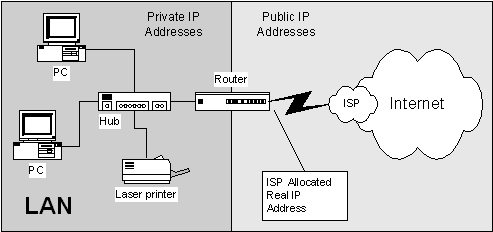
When connecting this network to the Internet, company XYZ will need a router (or computer acting as a router) to connect to the Internet and an ISP to obtain a connection that is either dial-up or permanent. If the connection is a dial-up service then the ISP will allocate your router an IP address dynamically. Each time you dial the ISP you may get a different IP address. This IP address will be allocated out of a pool of addresses managed by the ISP and are not in the 192.168.1.0 network. If you have a permanent connection to the Internet then your ISP will allocate you a fixed IP address for the Internet side of your router. This address will be part of the ISPs network. Note that routers need IP addresses for each interface on the router that is connected to a separate IP network.
To use your private IP addresses and be able to talk to the Internet you will need NAT (Network Address Translation) enabled in your router, otherwise you would need to obtain a set of real public IP addresses from your ISP for you LAN.
Company "Bigger Than XYZ" has two sites in the same city that need to be connected together. Lets call these sites A and B.

These sites are connected using a leased line service from a local telecommunications company. As the digram above shows, there are 2 LANs which, when connected form a WAN. In all, there are three (3) separate IP networks, separated by the routers. That is, LAN A and LAN B are two separate IP networks and the interconnecting link is a third IP network.
To allocate IP addresses to the nodes on this network we need to design an IP address space with three networks or subnets. Lets assume that these networks need up to 254 addresses. We now have a couple of options. These are:
Assuming we are going to always use private IP addresses then the first option is simple and we could allocate the following:
| LAN A | 192.168.1.0 |
| LAN B | 192.168.2.0 |
| WAN Link | 192.168.10.0 |
These addresses have been arbitrarily chosen from the private IP addresses for a C class network.
If we were already using a B class network of 172.24.0.0 then we could subnet this into 3 or more subnets. Allowing room for network growth we might decide to use 3 bits of the host ID for subnetting which would give us a maximum of (23 - 2) = 6 subnets and (213 - 2) = 8190 nodes per subnet. Thus our subnet mask would be:
255.255.224.0 or 11111111 11111111 11100000 00000000
As you can see from the binary form of the subnet mask, there are 13 bits of host ID and 19 bits of network ID (made up of the 16 bits of standard B class network ID and 3 bits of subnet ID).
The allowable networks from this choice of address and subnet mask would be:
| Network Address (3rd Octet in Binary) |
Network Address (Decimal) |
Broadcast Address (3rd Octet in Binary) |
Broadcast Address (Decimal) |
| 172.24. 00100000 .0 | 172.24.32.0 | 172.24. 00111111 .255 | 172.24.63.255 |
| 172.24. 01000000 .0 | 172.24.64.0 | 172.24. 01011111 .255 | 172.24.95.255 |
| 172.24. 01100000 .0 | 172.24.96.0 | 172.24. 01111111 .255 | 172.24.127.255 |
| 172.24. 10000000 .0 | 172.24.128.0 | 172.24. 10011111 .255 | 172.24.159.255 |
| 172.24. 10100000 .0 | 172.24.160.0 | 172.24. 10111111 .255 | 172.24.191.255 |
| 172.24. 11000000 .0 | 172.24.192.0 | 172.24. 11011111 .255 | 172.24.223.255 |
For Each of these networks, the network address and broadcast address represent the lowest and highest addresses in that subnet and all the addresses in between can be allocated to nodes. For example, in network 172.24.128.0 with broadcast address 172.24.159.255, the allowable addresses would be:
172.24.128.1
172.24.128.2
.....
172.24.140.1 and so on....
.....
172.24.159.253
172.24.159.254
Company "The Biggest XYZ" has two sites in the same city that need to be connected together. Lets call these sites A and B. Site A is the main office and will also have an Internet connection to allow all staff at both sites to gain Internet access. Also, the company wants to have its own web server so a permanent Internet connection will be needed. The company has decided that the Web server will be on a separate network for security purposes. The diagram below shows this example in more detail.
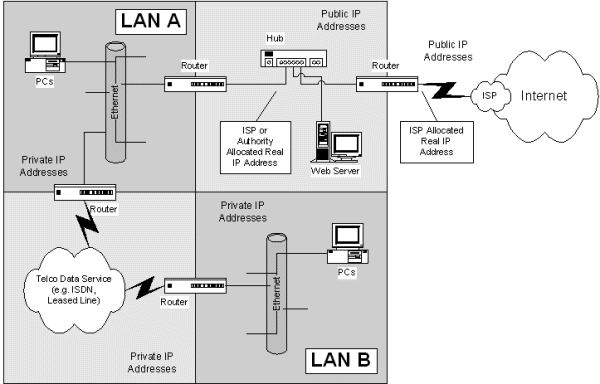
Lets assume they want to use a B class private IP Network address for ease of subnetting and room for expansion. Let's select 172.16.0.0 with a default subnet mask of 255.255.0.0. From the diagram above we can see that there are 2 LANs and one inter-LAN link which gives a total of 3 subnets. The network with the web server will be using real Internet assigned IP addresses because the company wants to host its own web server. These addresses can be obtained from your ISP or by applying for addresses from your local Internet number assigning authority.
To make it simple lets assume that both LANs A and B have fewer that 254 nodes (including the routers). We could then use the 4th octet for the host ID and the 3rd octet as the subnet mask. Thus the new subnet mask would be:
255.255.255.0
or
11111111 11111111 11111111 00000000
This gives us a series of networks like:
172.16.1.0
172.16.2.0
172.16.3.0 etc...
Lets assign 172.16.1.0 to LAN A, 172.16.2.0 to LAN B and 172.16.3.0 to the inter-LAN link. On the link you could give the router interfaces IP addresses of 172.16.3.1 and 172.16.3.2. The router interfaces on LAN A could get IP addresses like 172.16.1.1 and 172.16.1.2. Similarly for LAN B.
One question we have not answered is how does a router work or how does it know where to send a packet of information to in a multiple subnet network? We will look at these questions in the next section on routing.
We have mentioned routers several times already and have generally defined them as a device that connects different IP networks or subnets together and moves IP packets between them. This device can be a stand-alone dedicated network device or it can be software running on a computer with multiple network interfaces. In general terms routers have the following properties:
It now becomes obvious that for routers to work they need to have a picture of the network at any given time so that they know where to send packets to. Particularly on large networks (such as the Internet), routers need to be dynamically updated with information (or routes) so they can forward packets to their destinations correctly. If a router cannot find a route or has other problems when attempting to forward a packet then the router informs the sending node that a problem has occurred.
Routers maintain their picture of the network using a table of routes or a routing table. This table can be updated and added to, either dynamically or statically. Dynamic updates occur using routing protocols which distribute routing information around a network for all routers. Examples of these routing protocols include RIP (Routing Information Protocol) and OSPF (Open Shortest Path First). Static routes are manually added to routers by network administrators and do not change unless the administrator manually changes them.
Routing tables contain the following information:
As it would be impossible to record every route to every location in a large network it is common practice to have a default route which is a destination router that is responsible for forwarding packets when the initial router or host does not know where to forward the packet. Typically a router that acts as a default router will need to be more knowledgeable about the network than the router or host forwarding the packet.
So, how does all this actually work? Lets look at a node that wants to send a packet to a remote network. Typically if that node is a personal computer running an end user operating system (such as Microsoft Windows 98) then Windows makes a simple decision: is the destination on my local network? If the answer is yes then it sends it onto the LAN. If the answer is no then it must forward the packet according to its internal routing table. It is typical for routing tables on PC operating systems to simply have a default route which means Windows will forward the packet to a default router on the local LAN.
It is now the task of the default router to forward the packet towards its destination. It will also consult its routing table to see if the destination network is listed. If it is then it will know where to forward the packet and will do so. If not then it will use its own default route and forward the packet. This process continues until the packet reaches a router that is directly connected to the destination node. This last router will send the packet onto that network so the destination node can receive it.
If at any time the packet is received by a router that has no next hop for that destination then the router destroys the packet and sends an ICMP message back to the sender. ICMP stands for Internet Control Message Protocol and provides error reporting and network testing functions.
In simple networks that change infrequently it is common to use static routing. The process of setting up static routes is one where each router is told about how to send packets to other networks. Typically this takes the form of a command that looks something like this:
route ADD [destination] MASK [subnet_mask] [gateway] METRIC [num]
e.g. route ADD 157.0.0.0 MASK 255.0.0.0 157.55.80.1 METRIC 3
NOTE: The term "gateway", as used above, is equivalent to a router. Gateways are generally defined as devices used to interconnect different systems or networks.
On most UNIX and Windows systems you can use the "netstat -r" command to display the routing table.
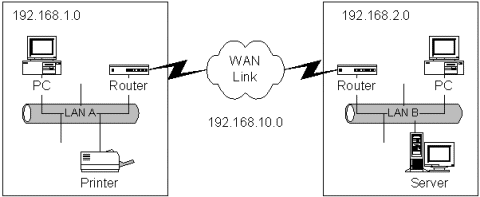
In the example network above we need to configure the routers with static routes so that LAN A and LAN B will be able to send IP packets to each other. Lets assign some addresses so we can setup static routes in the routers:
| Router in LAN A: | |
| IP address of LAN Interface: | 192.168.1.1 |
| IP Address of WAN Interface: | 192.168.10.254 |
| Router in LAN B: | |
| IP address of LAN Interface: | 192.168.2.1 |
| IP Address of WAN Interface: | 192.168.10.253 |
We will assume that all addresses are standard C class addresses using the default subnet mask of 255.255.255.0.
In this type of network, it is typical to configure the PCs to have default routes that point at the nearest router. So the PC in LAN A would have a default gateway of 192.168.1.1. Simimlarly in LAN B, the computers would be configured with their default gateway set to 192.168.2.1. Now, to setup the static routes in the routers we need to tell each router about how to get to the other LAN. You might think this was obvious but think about it from the routers perspective. If you were router A (i.e. the router connected to LAN A) then the only networks that you can actually see (the networks you are directly attached to) are 192.168.1.0 and 192.168.10.0. Router A does cannot see LAN B and does not know what is address is. So if Router A receives a packet that is going to address 192.168.2.17 then it does not know where to send it.
In router A you would configure a static route with the following information:
| Destination | Subnet Mask | Type | Gateway | Metric |
| 192.168.2.0 | 255.255.255.0 | Network | 192.168.10.253 | 1 |
Thus if router A receives a packet from LAN A and the destination is for network 192.168.2.0 then router A forward the packet to gateway 192.168.10.253. Note that gateways must be set to a directly reachable device. When 192.168.10.253 (router B) receives the packet it will read the destination address. When it sees that the destination is in the 192.168.2.0 network it will simply forward the packet onto LAN B since 192.168.2.0 is a directly connected network for router B.
Similarly for router B, we would set the static route with the following parameters:
| Destination | Subnet Mask | Type | Gateway | Metric |
| 192.168.1.0 | 255.255.255.0 | Network | 192.168.10.254 | 1 |
NOTES:
Type is included as there are two types of routes: host routes and network routes. Host routes are routes for a specific node's IP address.
The Metric value is set to the maximum number of hops that the packet will have to traverse to get to the destination. Every router the packet has to traverse is counted as one hop.
In large networks or in networks that change frequently, it becomes impractical to use static routes due to the high maintenance costs and possibility of configuration errors. In these cases a dynamic routing table update mechanism must be used employing one of the many routing protocols that routers currently support. One of the most widely used routing protocols is RIP (Routing Information Protocol). RIP is currently supported by most routers as well as many operating systems including Windows NT, Windows 2000 and most versions of UNIX. It is also possible to use a combination of static routes and routing protocols.
Many protocols make up the suite of protocols commonly referred to as TCP/IP protocols. IP is the network layer protocol of the TCP/IP suite. we will now examine some of the more common protocols that make up TCP/IP.
ICMP is a control protcol used mainly by routers to control the movement of packets and for reporting network problems. It is also commonly used for manual troubleshooting of IP networks. ICMP is a network layer protocol and is an integral part of IP. ICMP is a message based protocol and some of the message types are:
When an ICMP destination-unreachable message is sent by a router, it means that the router is unable to send the packet to its final destination. The router then discards the original packet. A destination may be unreachable because the source host has specified a nonexistent address or the router does not have a route to the destination.
Echo requests (commonly called a "ping") are generated by the "ping" command and are used to determine if hosts are reachable across the network. Echo replies are sent in response to echo requests. The ping command is used to test network problems such as routing configurations and is the first tool to use when diagnosing communication issues on IP networks.
An ICMP redirect message is designed to inform hosts of more efficient routes to destinations. Thus if a router receives a packet that would be better forwarded by a different router then it will still forward the packet but will also send an ICMP Redirect message to the sending host to tell it of the better route. This does not mean the host will always act upon this information.
An ICMP Time-exceeded message is sent by a router if an IP packet's Time-to-Live field (expressed in hops or seconds) reaches zero. The Time-to-Live field prevents packets from continuously circulating the network if the network contains a routing loop. The router then discards the original packet.
For more information on the ICMP protocol please refer to RFC 792.
TCP provides a reliable data delivery mechanism between two hosts on the IP network. TCP ensures that data is delivered by numbering packets for identification and retransmitting packets that are not received. TCP is a connection oriented protocol which means two hosts make a TCP connection and then use that connection to communicate reliably. The TCP connection needs to be established prior to communication and torn down after it is finished. Data transmission cannot begin until the establishment phase is complete.
A TCP connection is identified uniquely using a combination of the IP address of the host and a TCP port number which is associated with an upper layer application level protocol. Application level protocols usually have their own well known port numbers associated with them.
TCP is the transport protocol for many well know application level protocols such as TELNET, FTP (File Transfer Protocol) and SMTP (Simple Mail Transfer Protocol).
UDP is a connection-less protocol that simply acts as an interface between IP and the application layer process. UDP also uses port numbers to distinguish applications running on the same host, similar to TCP. UDP is different to TCP in that UDP does not provide any of the reliable delivery mechanisms. UDP is considered to be a "send and pray" protocol since you never know if the data actually got to the destination. Applications that use UDP frequently implement their own reliable transmission methods, instead of allowing the transport layer protocol (UDP or TCP) to perform this function.
UDP is the transport protocol for many well know application level protocols such as DNS (Domain Name System), SNMP (Simple Network Management Protocol) and TFTP (Trivial File Transfer Protocol).
DNS is an important protocol in most networks and especially in the Internet as it allows computers and people to use names instead of IP addresses when communicating between hosts. DNS allows names to be associated with IP addresses and provides mechanisms for these pairs to be dynamically updated and the changes propogated througout the network. Without DNS we would not be able to use names such as "http://www.ml-ip.com/" or "http://www.microsoft.com/" when using a web browser or use a command such as:
ping my_pc.company.com
DNS resolves these names into IP addresses so that the application can then communicate with the destination host. DNS is actually a network of DNS servers. If one DNS server doesn't know how to translate a particular domain name, it asks another one, and so on, until the correct IP address is returned.
When configuring hosts it is typical to tell the host the IP address of the nearest DNS server(s) as well as the domain name for that domain. The domain name is the portion of the full host name after the host name part. So, for the name "my_pc.company.com", the domain name is "company.com". Domain names are made up of multiple parts separated by periods ("."). The last part is a standard suffix such as "com", "org", "edu", "net" etc. Domain names are allocated by locall domain naming authorities so that the names remain unique for each region. Countries also typically have their own suffix as part of a domain name. Thus, the domain name "mycompany.com.au" would be a commercial organization in Australia.
Telnet is a terminal emulation program that allows you to remotely login to and access multi-user computer systems as if you were entering commands on the system's console. They are referred to as terminal emulation programs because they emulate a dumb terminal. Dumb terminals are devices made up of a monitor and keyboard and are directly connected to a multiuser host computer. Dumb Terminals do not have any local processing capabilities, hence the term "dumb". Telnet allows you to execute applications and commands on remote systems across an IP network. The host system must allow telnet access or, in other words, act as a telnet server. Telnet uses the TCP protocol and commonly uses TCP port 23 on the server for incoming telnet connections.
HTTP is the protocol used by the World Wide Web for transferring web page information, including text, graphics and much more. HTTP defines how messages are formatted and transmitted, and what actions Web servers and browsers should take in response to various commands. For example, when you enter a URL (Uniform Resource Locator) in your browser, this actually sends an HTTP command to the Web server directing it to fetch and transmit the requested Web page.
HTTP is called a stateless protocol because each command is executed independently, without any knowledge of the commands that came before it. This is the main reason that it is difficult to implement Web sites that react intelligently to user input.
The Point-to-Point Protocol (PPP) was developed to enable Local Area Networks that are remote from each other to be connected using point-to-point serial (asynchronous or synchronous) lines. It is the most popular method for remote users or branch office LANs to connect to a central LAN. PPP is also the dominant method for accessing the public Internet via a range of dedicated or dial-up access methods. Most consumers use PPP on their TCP/IP equipped personal computer and a dial-up modem to gain Internet access. PPP isn't only limited to TCP/IP networks and can carry other traffic such as IPX, AppleTalk, OSI, etc.
PPP encapsulates an IP datagram inside a PPP frame and relies on the serial interface (RS 232 dial-up port, V.35 dedicated line, etc.) to deliver it to the destination. In a TCP/IP network, a PPP connection has an IP address at each end, which are necessary for routing of packets. It provides a flexible and reliable link between two peers as it discards corrupted data and can negotiate compression and encryption.
In terms of the TCP/IP protocol stack, PPP sits at the Data Link Layer, just under IP. It receives packets from the IP layer adding headers and trailers to it before sending it on. The receiving end interprets these, strips them off and sends the packet up to the IP layer at the peer and so on. Therefore the transformations that PPP imposes are transparent to the upper layers.
To establish a PPP connection requires each end point to follow strict rules that can be grouped into four distinct phases: -
Password Authentication Protocol (PAP)
PAP is the simplest form of PPP authentication methods and uses the traditional
username and password authentication scheme. User credentials are sent in
clear text at the beginning of a session. The authenticating end validates
the information and replies with a positive or negative acknowledgement.
Challenge Handshake Authentication Protocol (CHAP)
CHAP uses a type of authentication that requires a challenge and a response.
The authenticating end challenges its peer with a CHAP name and a random string.
The client needs to transform the random string with a cryptographic function
and a secret key. Subsequently it returns the result with it own name. The
challenger compares the reply with the copy of the secret key and finally
a positive or negative acknowledgement is returned. All in all it is a three-way
handshake.
![]()
about ePipe | products | solutions | support | information center | contact us
Copyright © 2002 ePipe Pty. Ltd. All rights reserved.